Managed Solutions: Your Primary Line of Security in Cybersecurity

In the modern digital world, online security has evolved into a vital component for the smooth operation and success of businesses of all types. With the constantly changing barrage of online threats, from advanced ransomware threats to misleading phishing schemes, organizations must emphasize protecting their confidential data and infrastructure. The consequences have never been higher; a solitary incident can lead to severe monetary setbacks, loss of credibility, and legal issues. Businesses of every scale are recognizing that the primary safeguard against these threats is beyond merely relying on a dedicated IT staff but rather a holistic approach involving expert IT management.
Managed services provide businesses with expert skills and forward-thinking strategies to tackle the variety of cyber threats they face. By partnering with an IT managed services provider, companies can improve their security posture while gaining cost efficiencies, improved compliance, and a solid foundation for service resilience. Grasping the functionality of these solutions and their importance in current security practices can equip organizations to skillfully traverse the challenging realm of cybersecurity, ensuring they are prepared to defend against future invasions.
Grasping Cyber Security Threats
In the modern cyber landscape, comprehending cybersecurity risks is crucial for each business. The rapid advancement of technology has broadened the attack surface, making organizations more susceptible to cyber threats. Regardless of size, small and large businesses face an array of potential risks, including data breaches, ransomware, and phishing attacks. Failing to acknowledge these risks can lead to significant financial loss, damage to reputation, and regulatory consequences, underscoring the significance of emphasizing cybersecurity strategies.
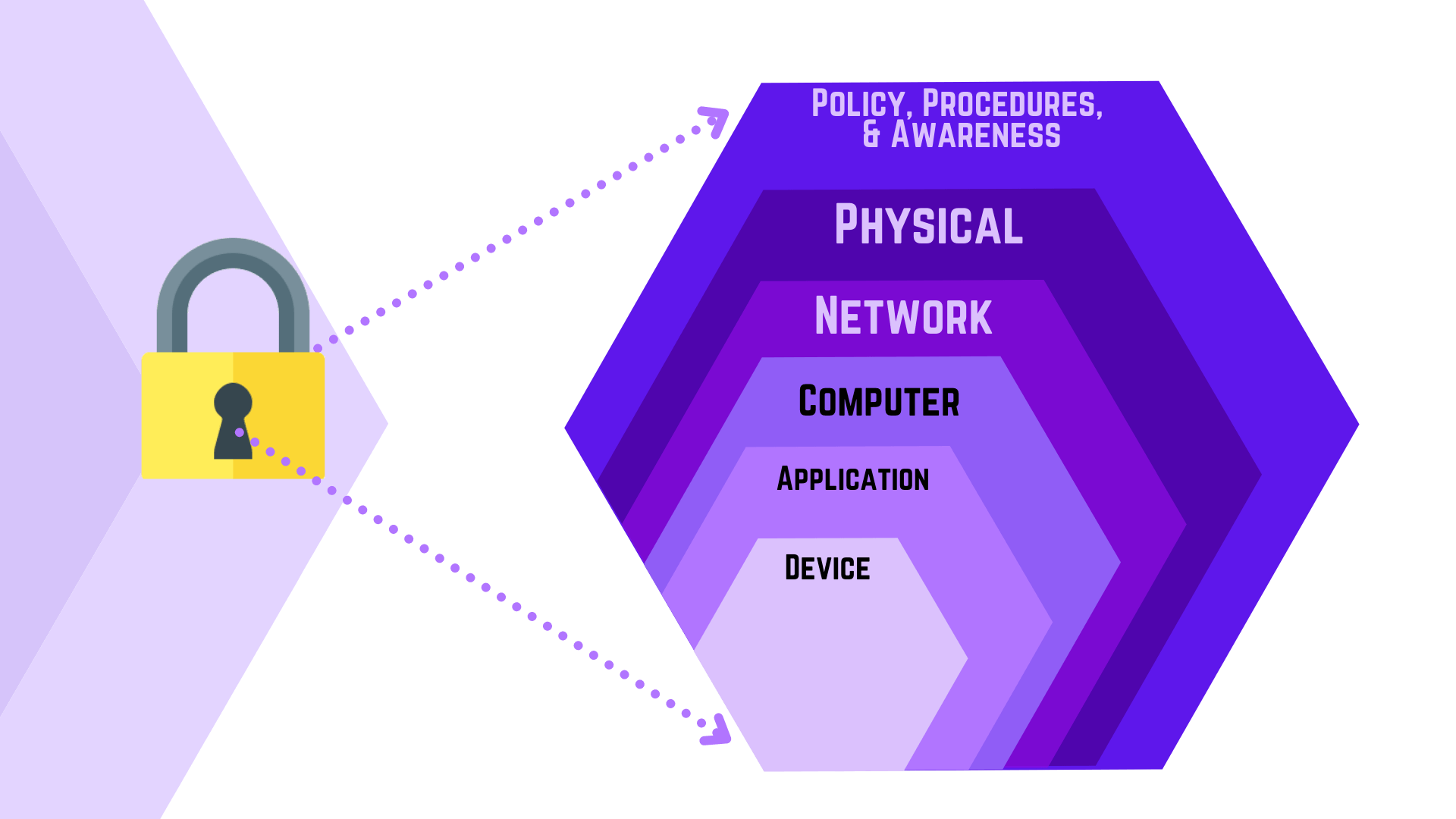
The most common cybersecurity threats come in multiple forms, every with its own features and prevention methods. Ransomware, for illustration, locks critical data until a fee is paid, while phishing scams fool employees into revealing sensitive information. Recognizing these threats and executing measures such as user education, regular security assessments, and maintaining up-to-date software can significantly reduce the risk of suffering from such attacks. Knowledge is strength, and staying informed about developing threats is crucial for effective defense.
Moreover, the implications of a cybersecurity breach extend beyond immediate financial loss. Businesses risk losing client trust and facing investigations, further highlighting the need for a proactive approach to cybersecurity. By analyzing potential vulnerabilities, creating a solid incident response plan, and investing in outsourced services, organizations can minimize risks effectively. A comprehensive understanding of these cybersecurity risks equips businesses to make informed decisions and emphasize security in their business strategies.
The Importance of IT Managed Services
IT managed services play a critical role in enhancing information security for businesses of various sizes. By delegating IT management to professional providers, organizations can take advantage of knowledge and resources that may not be accessible in-house. This access to cutting-edge security tools and technologies allows businesses to preventively address potential vulnerabilities and threats. MSPs offer a all-encompassing approach to cybersecurity, encompassing everything from threat detection and response to compliance management, ensuring that businesses stay ahead of evolving online threats.
One significant advantage of IT managed services is the constant monitoring and support they provide. MSPs employ skilled experts who monitor infrastructure 24/7, quickly identifying and responding to issues that could indicate a cyber breach. This preventive monitoring minimizes downtime and mitigates the threat of impact of security incidents, enabling businesses to keep operations efficiently. Furthermore, managed services can help streamline routine security tasks, freeing up internal resources to prioritize innovation efforts that drive development and innovation.
Moreover, IT managed services help businesses establish robust cybersecurity policies and best practices tailored to their unique needs. This includes the implementation of multi-factor authentication, secure data protocols, and endpoint protection. MSPs also provide training for employees on recognizing social engineering tactics and other common threats, which significantly enhances the overall safety measures of the organization. By embedding managed Thales Ciphertrust Manager into their cybersecurity strategies, businesses not only fortify their defenses but also cultivate a security-conscious environment that is crucial in today’s digital landscape.
Best Practices for Business Security
Adopting robust security measures is important for safeguarding your business from digital threats. Regular employee training on cybersecurity awareness is one of the top practices, helping staff spot phishing scams and questionable activities. Frequent workshops can empower employees with knowledge about the latest threats and how to combat them, developing a culture of security within the organization. Promoting a proactive approach to security among all team members can significantly reduce the risk of completed attacks.
A further key practice is the implementation of multi-factor authentication for accessing sensitive systems and data. This added layer of security makes it much harder for unauthorized users to gain access, even if they successfully gain passwords. It is essential that businesses implement MFA across their platforms to enhance security, specifically for remote work setups or when accessing cloud services. Ongoing monitoring and updating of access controls should also be a priority to ensure that only authorized personnel have access to sensitive information.
Furthermore, maintaining comprehensive data backup and disaster recovery plans is essential. This practice ensures that, in the event of a security incident or data loss, businesses can quickly recover operations with reduced downtime. Frequently testing these backup systems and disaster recovery protocols will ensure they operate effectively when needed. By prioritizing these strategies, businesses can protect their data, enhance their robustness against cyber threats, and ensure they are well-prepared to react to incidents swiftly and efficiently.
